How SSL Protects Your eCommerce Transactions
SSL (TLS) is how eCommerce stores ensure that their customer’s data is kept private. We explain what SSL is and how it works.
 Last year, for the first time, eCommerce sales exceeded $1 Trillion. 1,000,000,000,000 dollars were sent whizzing around the Internet by online shoppers. That’s a huge amount of money, and its transfer usually involves the use of credit card numbers and personal details that hackers and identity thieves would love to get their hands on.
eCommerce transactions are protected by a technology commonly known as SSL (Secure Socket Layer), or more properly, TLS (Transport Security Layer). We’ll stick with calling it SSL, since that is how it’s more commonly known outside of technical circles.
You can tell when your connection to a server uses SSL by looking in the address bar of your web browser. Instead of “http://” the beginning of the web address will read “https://” and there will be a small graphic to indicate an SSL connection, usually a green padlock.
Last year, for the first time, eCommerce sales exceeded $1 Trillion. 1,000,000,000,000 dollars were sent whizzing around the Internet by online shoppers. That’s a huge amount of money, and its transfer usually involves the use of credit card numbers and personal details that hackers and identity thieves would love to get their hands on.
eCommerce transactions are protected by a technology commonly known as SSL (Secure Socket Layer), or more properly, TLS (Transport Security Layer). We’ll stick with calling it SSL, since that is how it’s more commonly known outside of technical circles.
You can tell when your connection to a server uses SSL by looking in the address bar of your web browser. Instead of “http://” the beginning of the web address will read “https://” and there will be a small graphic to indicate an SSL connection, usually a green padlock.
 If a company sends your browser a certificate that has been signed using the private key of a Certificate Authority, you can be almost completely certain that the server you are connected to belongs to who you think it does.
If a company sends your browser a certificate that has been signed using the private key of a Certificate Authority, you can be almost completely certain that the server you are connected to belongs to who you think it does.
 Last year, for the first time, eCommerce sales exceeded $1 Trillion. 1,000,000,000,000 dollars were sent whizzing around the Internet by online shoppers. That’s a huge amount of money, and its transfer usually involves the use of credit card numbers and personal details that hackers and identity thieves would love to get their hands on.
eCommerce transactions are protected by a technology commonly known as SSL (Secure Socket Layer), or more properly, TLS (Transport Security Layer). We’ll stick with calling it SSL, since that is how it’s more commonly known outside of technical circles.
You can tell when your connection to a server uses SSL by looking in the address bar of your web browser. Instead of “http://” the beginning of the web address will read “https://” and there will be a small graphic to indicate an SSL connection, usually a green padlock.
Last year, for the first time, eCommerce sales exceeded $1 Trillion. 1,000,000,000,000 dollars were sent whizzing around the Internet by online shoppers. That’s a huge amount of money, and its transfer usually involves the use of credit card numbers and personal details that hackers and identity thieves would love to get their hands on.
eCommerce transactions are protected by a technology commonly known as SSL (Secure Socket Layer), or more properly, TLS (Transport Security Layer). We’ll stick with calling it SSL, since that is how it’s more commonly known outside of technical circles.
You can tell when your connection to a server uses SSL by looking in the address bar of your web browser. Instead of “http://” the beginning of the web address will read “https://” and there will be a small graphic to indicate an SSL connection, usually a green padlock.
What Is SSL?
When you want to send information securely, it’s important that you know two things. Firstly, that you are sending the information to the right person or organization, and secondly, that no one can read that information while it’s on the way. SSL services like Comodo or WP Force SSL allows eCommerce shoppers to be certain of both the identity of the server they are communicating with and the privacy of the information they are sending.What Are Public Key Cryptography And Symmetric Encryption?
To understand how SSL works, it’s first necessary to understand the basics of two different sort of encryption and identity verification. Public-key encryption is widely used on the Internet. It’s a complex topic and if you want the full skinny, you should check out the excellent Wikipedia article. But, in short, public-key cryptography relies on the use of two different keys, one public, and the other private. The private key is a strictly guarded secret; the public key can safely be known by anyone. The public key is used to encrypt content that can only be decrypted by the private key. Additionally, the private key can be used to cryptographically sign information sent over the Internet to verify the identity of the sender. Symmetric cryptography is the more familiar type of encryption, where one key is used to both encrypt and decrypt information.How Does SSL Guarantee I’m Sending Information To The Right Place?
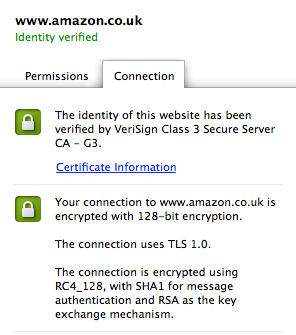
It is possible for a hacker to trick people into going to a site that looks exactly like their bank’s site or an eCommerce store in order to get them to enter sensitive information. So, it’s necessary that, when conducting private business on the Internet, there is a way to verify that your browser is connected to a legitimate server. After an SSL connection has been established between a server and your browser, the server will send a digital certificate that has been signed using the private key of an organization that your browser trusts. To do that, your browser has to have the public key that goes with the private key that was used to sign the certificate. It’s not possible for your browser to store all the public keys of every site you might want to visit — there would be millions of them — so there are a number of organizations, known as Certificate Authorities, that use their private key to sign the certificates of companies that you might want to buy something from. For example, Amazon.com have had their certificate signed by VeriSign, which is a prominent Certificate Authority. Your browser knows the public keys of the Certificate Authorities and implicitly trusts certificates that have been signed by them. You can click on the green padlock in your address bar and it will show you which CA signed the certificate of the site you are connected to. If a company sends your browser a certificate that has been signed using the private key of a Certificate Authority, you can be almost completely certain that the server you are connected to belongs to who you think it does.
If a company sends your browser a certificate that has been signed using the private key of a Certificate Authority, you can be almost completely certain that the server you are connected to belongs to who you think it does.
How Does SSL Protect My Information When I Send It?
Now that your browser has verified that it is connected to the right people, it generates what is known as a pre-master key, encrypts it with the server’s public key from the certificate, and sends it to the server. The server decrypts the pre-master key, and then both the browser and the server perform a number of algorithmically determined operations on the pre-master key, which generates a master key. The master key is then used to generate session keys. The session keys are used to symmetrically encrypt all of the information traveling between the server and the browser. The above explanation is something of a simplification, and we’ve omitted a couple of details for the sake of clarity. If you want to know more, check out the additional resources at the end of the article. When implemented properly, this system is almost completely secure. Even if someone was listening in on the communication, they can’t know the session keys, because they don’t have access to the private keys of the server’s organization. And, if they were sitting in-between the browser and the server intercepting the communication, the encrypted information that they steal is practically impossible to decrypt. It is theoretically possible, but given the state of current technology, it would take them longer than the age of the universe to do so. SSL is an extremely reliable method of ensuring that private communication between eCommerce vendors and their clients remain secure. SSL certificate is compulsory for ecommerce businesses, so don’t wait more! Just choose a reliable and cheap SSL certificate provider to secure your client’s personal information and online transactions.Additional Resources
- TLS on Wikipedia
- Digital Signatures On Wikipedia
- How Does SSL Work?
- SSL/TLS certificates: What You Need To Know
About the Author
Graeme Caldwell works as an inbound marketer for Nexcess, a provider of Magento and WordPress hosting. For more information on eCommerce, hosting technologies, and other tech-related stuff, check out their blog at http://blog.nexcess.net/.

NICE POST